Scan Rules
In this section it is explained how the scan rules works.
When a scan is running, it will register one or more states to describe if there is something wrong in your Joomla!. A scan can register all these possible states:
- OK - the scan hasn't found anything wrong (all right).
- NOTICE - a state containing a notification for the administrator (nothing to worry about).
- WARNING - there is something suspicious (it is better to investigate).
- CRITICAL - it is needed to check the details of the state because the website may contain a malware.
Big Files
This rule is used to search for big files stored in the File System of the server.
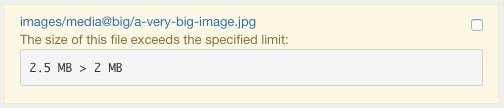
Every time the system finds a file with a size higher than the specified amount (see params), that file will be marked as a warning state.
Params
- File Size - the minimum size (in MegaBytes) of the files to looking for.
If you need to use a kB unit (or something lower), it is possible to insert a decimal amount (e.g. 0.8 MB is equals to 800 kB).
States
An OK message is raised if there are no files with a size higher than the specified one.

If the rule is not able to find any file, the plugin will register a NOTICE containing the file with the highest size (always lower than the specified amount).
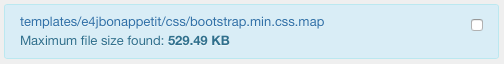
All the files that exceed the specified limit will be registered within a WARNING message.
Approve
For known big files that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
The known files are registered in combination with their size, this means that they won't be skipped if their size changes.
Make Safe
This rule doesn't have a method to make the file safe.
If you think a big file shouldn't be there, you can consider to delete it from the file system. Otherwise, you can approve it through the apposite button.
Code Obfuscation
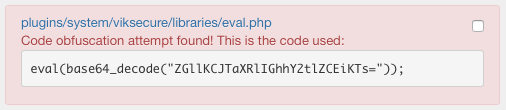
This rule is used to identify code obfuscation attempts. It searches for all the files that use the native eval() PHP function.
The eval() language construct is very dangerous because it allows execution of arbitrary PHP code. This means that it can be used to obfuscate the code or to execute code passed via GET (see the examples below).
eval(base64_decode("ZGllOw=="));This example decodes the "ZGllOw==" string (which is equals to "die;") and then executes the code. In this way, the website will die and you won't be able to recognize it. Usually this code is used to obfuscate a portion of code.
eval(base64_decode($_GET['code']));This example decodes a dynamic string passed via GET (e.g. code=ZGllOw%3D%3D) instead. If you find something like this on your website, it may mean that you server has been hacked, because anyone will be able to run custom code simply by visiting that file via browser.
Params
This rule doesn't use additional parameters.
Since this rule can handle only PHP files, the File Filter global setting is never used here.
States
An OK message is raised if there are no files containing code obfuscation attempts.

All the files that contain at least a code obfuscation will be registered within a CRITICAL message.
Each message will show also all the obfuscation attempts.
Approve
For known code obfuscations that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
The known files are registered in combination with their codes, this means that they won't be skipped if the obfuscations change.
Make Safe
This rule doesn't have a method to make the file safe.
If you think a file should contain that code, you can consider to approve it. Otherwise it is suggested to read that file to check if the code used may be dangerous or not.
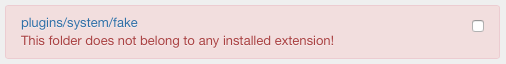
Fake Extensions
This rule is used to search for plugins, templates, components and modules that haven't been installed through the Joomla! Extensions Manager.
This helps to identify folders that seem real Joomla! installers but that may do something dangerous instead.
Params
This rule doesn't use additional parameters.
Since this rule can handle only FOLDERS, the File Filter global setting is never used here.
States
An OK message is raised if all the folders belong to installed extension.
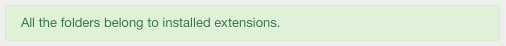
All the folders that don't belong to any installed extension will be registered within a CRITICAL message.
Approve
For known fake extensions that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
Make Safe
This rule doesn't have a method to make the file safe.
If you think a fake extension shouldn't be there, you can consider to remove the whole folder.
Htaccess Hack
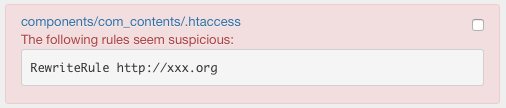
This rule is used to search for bad .htaccess files.
A .htaccess file is considered suspicious if it contains at least one of these rules: auto_prepend_file, auto_append_file, RewriteRule http.
The rules auto_append_file and auto_prepend_file include other PHP files at the beginning, or at the end, of the original PHP files, so that the attackers may use this tool to include their own code.
The RewriteRule http command may include malicious external redirects.
Params
- Ignore Main - when this option is enabled, the system will ignore the .htaccess file located in the root of the Joomla! website.
Enable this option only if you are sure that your main (in the root) .htaccess file doesn't own dirty code.
Since this rule can handle only HTACCESS files, the File Filter global setting is never used here.
States
An OK message is raised if there are no .htaccess files containing dirty code.

All the .htaccess files that contain at least a dangerous rule will be registered within a CRITICAL message.
Approve
For known .htaccess that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
The known files are registered in combination with their rules, this means that they won't be skipped if the code changes.
Make Safe
This rule doesn't have a method to make the file safe.
If you think a file should contain that code, you can consider to approve it. Otherwise it is suggested to read that file to check if the code used may be dangerous or not. if the whole file shouldn't be there, you can consider to remove it from the file system.
Joomla Safe Heading
This rule is used to find all the PHP files that do not start with a valid Joomla! Safe Heading.
A heading is considered safe if the first PHP line of a file stops the flow if someone is reaching that file via URL. For example:
defined('_JEXEC') or die;This technique is used by Joomla! to run PHP files only if we are visiting the website from the main index.php file.
All the possible Joomla! safe headings are: _JEXEC, JPATH_BASE, JPATH_PLATFORM, _AKEEBA_RESTORATION, FOF_INCLUDED.
Params
This rule doesn't use additional parameters.
Since this rule can handle only PHP files, the File Filter global setting is never used here.
States
An OK message is raised if all the files contain a Joomla! Safe Heading.

All the empty files (with null size) will be registered in a WARNING message.
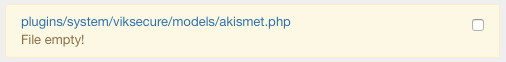
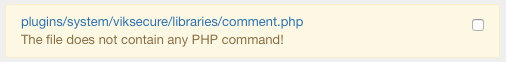
All the files that don't contain any PHP command will be registered in a WARNING message.
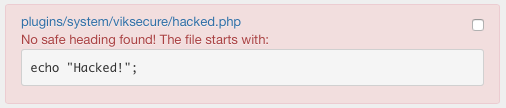
All the files that don't start with a safe heading will be registered within a CRITICAL message.
Approve
For known safe headings that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
The known files are registered in combination with their headings, this means that they won't be skipped if the first PHP line changes.
Make Safe
If a file can be considered safe and it doesn't own a Joomla! Safe Heading, it is possible to press the Make Safe button to insert at the beginning of the file the code below.
// No direct access to this file
defined('_JEXEC') or die('Restricted access');In this way, that file will be no more accessible by reaching it via URL.
System Information
This rule is used to check a few information about the system. Here's a list of all the things checked by the rule:
- total number of files stored in your server
- total size of the files stored in your server
- total number of database tables
- total number of database records
- total database size
- whether the default temporary folder (/tmp) contains some files
- file permissions
- folder permissions
Params
- Files Permissions - insert the permissions (e.g. 644) that all the files in your system should own. Leave empty if you don't know the default permissions of your files.
- Folders Permissions - insert the permissions (e.g. 755) that all the folders in your system should own. Leave empty if you don't know the default permissions of your folders.
Leave these 2 fields empty to let the system detecting the default permissions used by your files and folders.
States
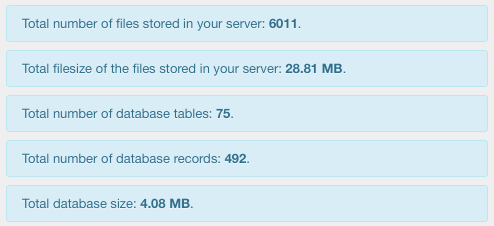
The information about the files and the database are always reported within a notice box.
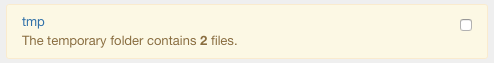
The temporary folder may contain files that should be no more accessible by the customers. So, it is always suggested to leave this folder empty. In case the temporary folder is not empty, the error message below will be raised. You can click the tmp link to see the list of the files stored in that folder.
The system will check for files and folders that don't match the default/specified permissions. In case of mismatched permissions, the error message below will be raised.
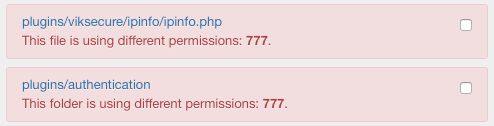
Approve
For known files and folders that have been detected, you can select them and press the Approve button. In this way, they won't be detected anymore during the scan.
The known files/folders are registered in combination with their codes permissions, this means that they won't be skipped if the permissions change.
Make Safe
It is possible to use this feature in order to fix the permissions of all the selected files and folders. For example, in case the system detected a few files with 777 permissions, the system will adjust them to the default/specified ones, which should be 644.